


Targeted attacks: Targeted attacks occur when cybercriminals focus on specific industries like healthcare, finance, and critical infrastructure, aiming for high disruption and financial gain. These attacks involve detailed reconnaissance and customized malware for the victim’s environment, highlighting the need for robust threat intelligence.
Supply chain attacks: Supply chain attacks increase risks by expanding ransomware’s reach. Attackers now target third-party vendors to access their customers’ networks, multiplying the impact and complexity of ransomware attacks, which calls for enhanced threat intelligence measures.
Double extortion: Double extortion, a tactic where cybercriminals encrypt data and steal sensitive information, threatening to release it unless a ransom is paid, increases pressure on victims to comply. This extortion tactic underscores the evolving nature of ransomware strategies.
Ransomware-as-a-Service: RaaS has democratized ransomware attacks, enabling non-technical individuals to launch sophisticated attacks easily. RaaS provides cybercriminals with advanced tools and infrastructure in exchange for a share of the ransom payments, making ransomware services more accessible.
Understanding common cybercriminal tactics is essential for effective ransomware defense. Tactics like phishing and exploiting vulnerabilities in software, networks, or systems are prevalent. Organizations must adopt comprehensive vulnerability management strategies to protect against ransomware, including phishing prevention and patching known vulnerabilities to mitigate risks.
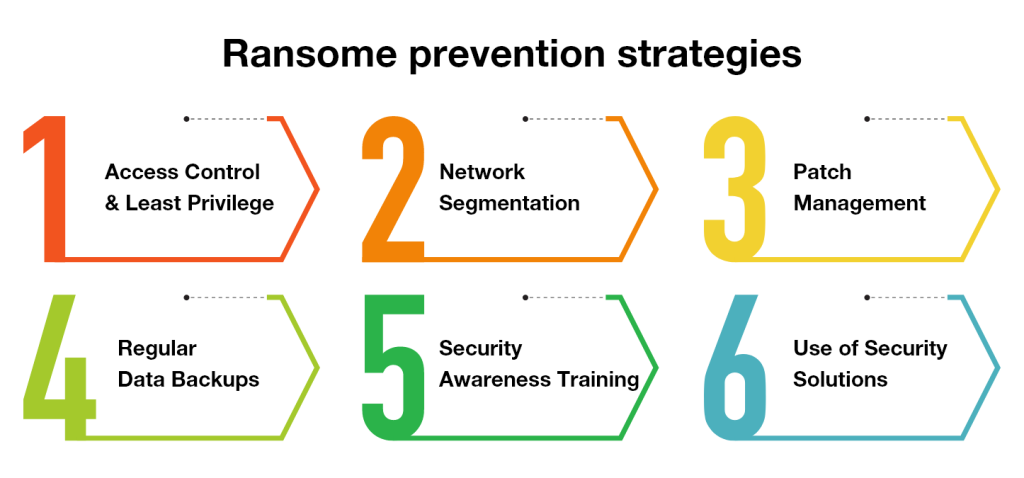
1. Access Control and Least Privilege: Implement strong access controls and adhere to the principle of least privilege to limit user access to critical systems and data. Restricting access reduces the risk of unauthorized actors gaining control over sensitive resources, a key strategy in ransomware prevention.
2. Network Segmentation: Implement network segmentation to effectively contain the spread of ransomware in case of a breach. By isolating critical systems and segmenting network traffic, organizations can significantly minimize the impact of an attack, highlighting a strategic approach on how to protect against ransomware through network segmentation.
3. Patch Management: Diligently keep software, operating systems, and applications up to date with the latest security patches to mitigate the risk of exploitation through known vulnerabilities. This patch management strategy is crucial for maintaining software updates and securing systems against potential threats.
4. Regular Data Backups: To protect against ransomware, perform regular data backups of critical data and store them securely offline or in a separate, isolated network environment. This proactive measure allows organizations to restore data without resorting to paying a ransom in an attack, emphasizing the importance of regular data backups in ransomware defense strategies.
5. Security Awareness Training: Educate employees about the risks of ransomware and provide comprehensive training on how to identify phishing attempts, avoid clicking on suspicious links or attachments, and maintain good cybersecurity practices. This security awareness training is a key component in teaching staff how to avoid ransomware and safeguard organizational assets.
6. Use of Security Solutions: Deploy advanced security solutions like endpoint detection and response (EDR), intrusion detection systems (IDS), and email filtering to detect and neutralize ransomware threats in real time. Leveraging ransomware solutions and managed detection and response technologies plays a critical role in an organization’s defense strategy.
The relentless evolution of ransomware attacks demands a proactive and multi-layered approach to cybersecurity. Organizations that remain vigilant by understanding current cybercriminal tactics and implementing robust ransomware prevention strategies, including threat intelligence, can significantly mitigate the risk of falling victim. This proactive approach safeguards critical assets and data, ensuring business continuity and minimizing disruption.
By combining technical controls, such as firewalls and intrusion detection systems, with employee education programs that emphasize cybersecurity awareness and best practices, organizations can build a robust defense against ransomware. Additionally, proactive risk management practices, including regular vulnerability assessments and penetration testing, are essential for ransomware readiness and preparedness, helping to maintain cyber hygiene and protect against potential attacks.
Do not wait for a ransomware attack to disrupt your operations. For any security concerns, do not hesitate to reach out to People Tech Group for personalized cybersecurity services – we have your back, offering tailored ransomware solution options to meet your specific needs.
